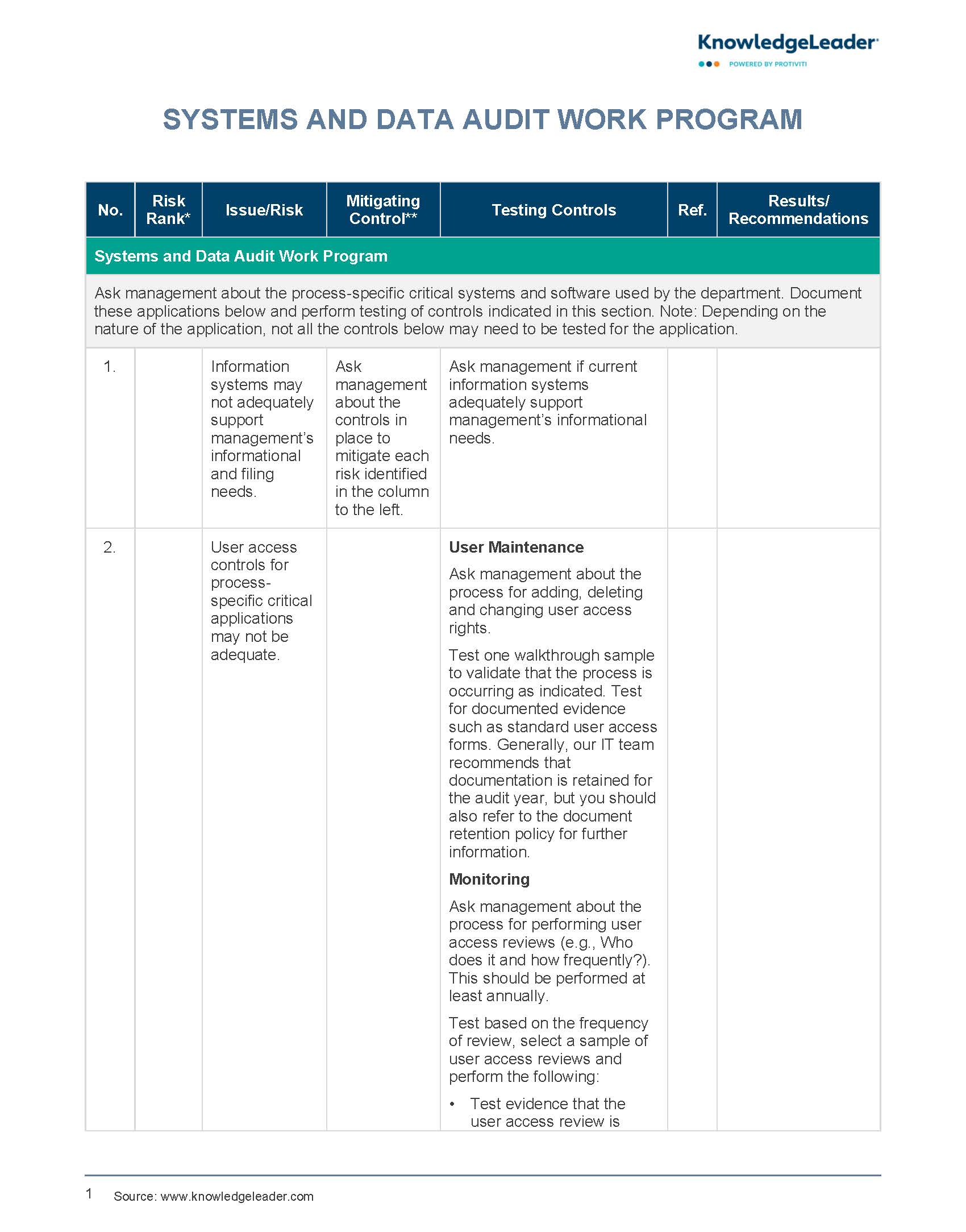
Systems and Data Audit Work Program
Subscriber Content
Preview Image
Image
Best Practices for Auditing Systems and Data Security
This sample work program can be used by auditors to identify and mitigate risks associated with an organization’s critical systems and software.
Sample steps include asking management about the process for adding, deleting and changing user access rights; asking management about the process for performing user access reviews; testing evidence that the user access review is performed; confirming that users have a business need for their access; determining whether duties are appropriately segregated; assessing the security settings for appropriate segregation of duties; reviewing controls over user administration; and monitoring the appropriateness of user access.
Related Resources