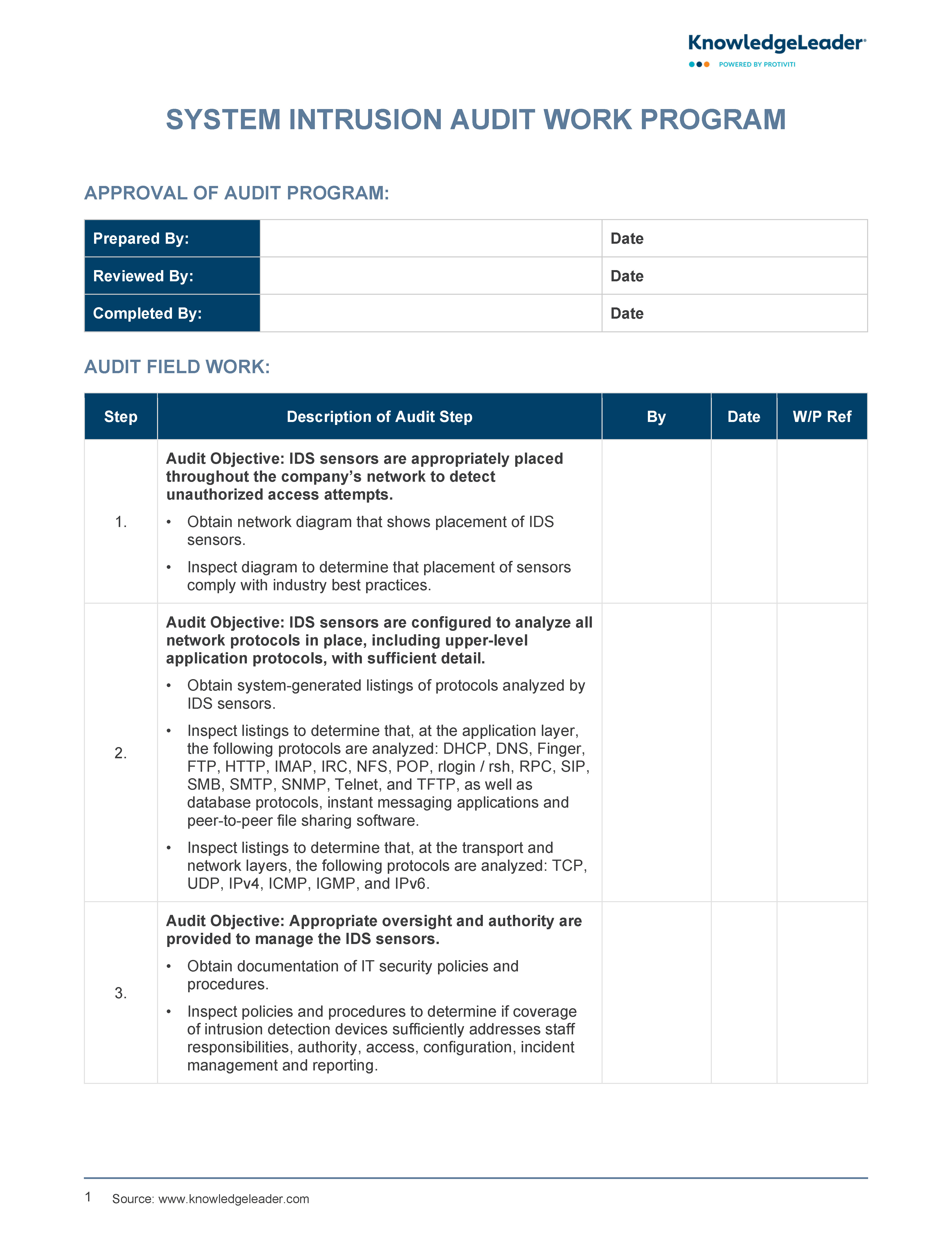
System Intrusion Audit Work Program
A Comprehensive Plan for Detecting and Mitigating Cyber Threats
Use our System Intrusion Audit Work Program to conduct thorough audits on intrusion detection systems (IDS) within your organization’s IT infrastructure.
This sample provides a structured approach to evaluating the effectiveness and compliance of IDS sensors deployed across the network. It outlines specific audit steps aimed at verifying the strategic placement and configuration of IDS sensors to monitor various network protocols effectively, both at application and transport layers. Furthermore, it assesses the management of IDS, including policy approval, incident response times, update authenticity and logical access controls by authorized personnel. This work program also addresses the need for physical security measures to protect IDS hardware from unauthorized access or environmental threats.
Overall, this tool is vital for ensuring that an organization’s intrusion detection capabilities are robust, adhere to best practices, and align with internal IT security policies and procedures. This thorough audit assists in mitigating risks by identifying vulnerabilities and ensuring that responsive measures are in place to handle potential security breaches effectively.
Sample audit steps include:
- Obtain the system-generated listings of protocols analyzed by the IDS sensors.
- Obtain a network diagram that shows the placement of IDS sensors.
- Inspect the diagram to determine that the placement of sensors complies with industry best practices.